Hopefully it is well known by now that two-factor/multi-factor authentication (MFA) is not a silver-bullet to all your cyber problems.
The tooling – Evilginx
I previously wrote about Evilginx and how we are starting to see it more and more, even though the original tool was developed back in 2017: https://github.com/kgretzky/evilginx2

What is it?
Evilginx is a open-source reverse-proxy phishing framework, designed to provide red-teamers/penetration testers the ability to bypass MFA.
How does it work?
To overly simplify, the tool works as an Adversary-in-the-middle. The user could be socially engineers to authenticate into their account through a malicious shell-site, delivered via phishing email as one example. Evilginx is sitting in the middle to collect the precious web traffic during the legitimate authentication workflow conducted by the user. The output; a session cookie, providing access to the account after the attack-chain is complete.
John Hammond has created an excellent demonstration video showcasing how the tool can be used to bypass MFA. The example showcases bypass of MFA in a Microsoft 365 (M365) environment; the cloud platform I see used most commonly by organisations for email hosting.
The snippet below showcases the execution from the adversary, after the victim has been socially engineered to click the link and sign-in to their M365 account on the fake web-shell site.
The full ~20 minute video is worth a watch if you’re interested in the complete end-to-end process.
The requirements
There are some precursors to this methodology to successfully bypass MFA:
- Attacker knows their victims email address.
- Attacker knows the victim has an account with the platform (i.e. M365)
- Victim receives phishing email (isn’t blocked by an email filter).
- Victim is susceptible to social engineering.
Above all else, the victim must engage with the phishing email, enter their credentials as well as the MFA code or approve the MFA push notification received on the mobile phone. Most importantly, they mustn’t inspect the URL to the link they clicked, which would point out the suspicious shell-site!
Defending against MFA bypass
How can organisations protect themselves against session cookie theft? Microsoft, in respect to the example above, have controls to prevent this attack vector: https://learn.microsoft.com/en-us/entra/standards/memo-22-09-multi-factor-authentication

The creator of Evilginx (@mrgretzky) has even confirmed that these security controls are sufficient in blocking reverse-proxy phishing! The attacker technique used to bypass MFA.
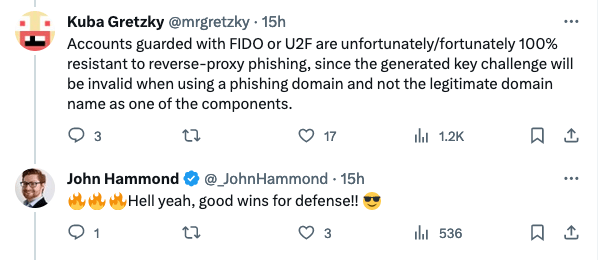
However, Evilginx and other frameworks are not just applicable to Microsoft 365. They can be used by an adversary across any web-platform, from what I can tell. So it is up to each individual vendor to implement similar or alternative controls to protect users against this type of trade-craft.

Leave a comment